
US Defence Secrets Targeted By Russian Hackers

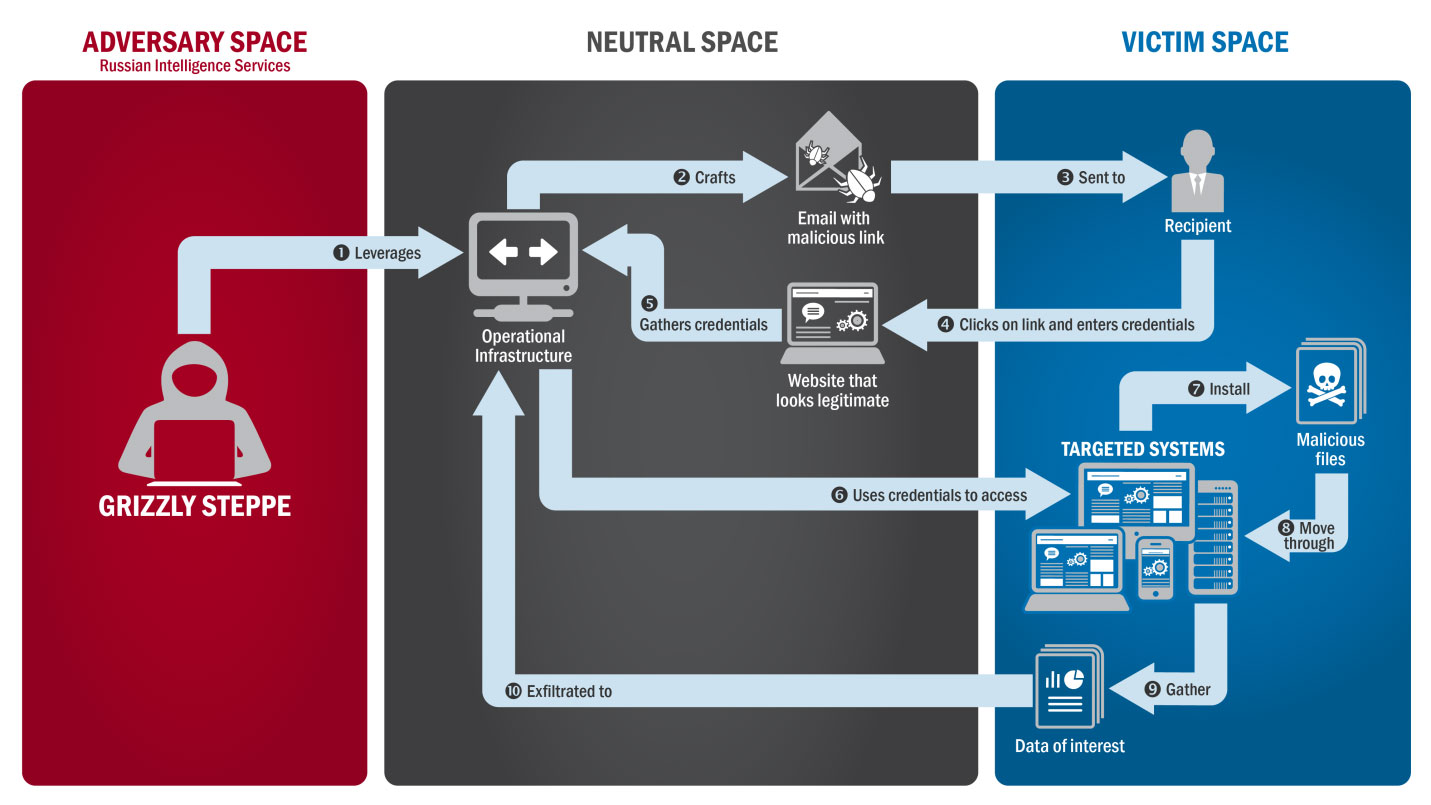
Russian cyberspies pursuing the secrets of military drones and other sensitive USdefence technology tricked key contract workers into exposing their email to theft, an investigation has found.
What ultimately may have been stolen is uncertain but the hackers clearly exploited a national vulnerability in cybersecurity: poorly-protected email and barely any direct notification to victims, according to Associated Press (AP).
The hackers, part of a group known as 'Fancy Bear', went after at least 87 people working on militarised drones, missiles, rockets, stealth fighter jets, cloud-computing platforms or other sensitive activities, AP found.
Employees at both small companies and largerdefence manufacturers like Lockheed Martin, Raytheon, Boeing, Airbus Group and General Atomics were targeted by the hackers.
A handful of people in Fancy Bear's sights also worked for trade groups, contractors in US-allied countries or on corporate boards.
"The programmes that they appear to target and the people who work on those programmes are some of the most forward-leaning, advanced technologies," said Charles Sowell, a former senior adviser to the US Office of the Director of National Intelligence, who reviewed the list of names for the AP.
Mr Sowell, who was one of the hacking targets, said:
"If those programmes are compromised in any way, then our competitive advantage and ourdefence is compromised. That's what's really scary."
AP identified thedefence and security targets from about 19,000 lines of email phishing data created by hackers and collected by the US-based cybersecurity company Secureworks, which calls the hackers Iron Twilight.
The data is partial and extends only from March 2015 to May 2016. Of 87 scientists, engineers, managers and others, 31 agreed to be interviewed by AP.
Most of the targets' work was classified, yet as many as 40% of them clicked on the hackers' phishing links, the AP analysis indicates.
That was the first step in potentially opening their personal email accounts or computer files to data theft by the digital spies.
James Poss, who ran a partnership doing drone research for the Federal Aviation Administration, was about to catch a taxi to the 2015 Paris Air Show when what appeared to be a Google security alert materialised in his inbox.
Distracted, he moved his cursor to the blue prompt on his laptop.
"I clicked on it and instantly knew that I had been had," the retired Air Force major general said.
Mr Poss says he realised his mistake before entering his credentials, which would have exposed his email to the hackers.
Hackers predominantly targeted personal Gmail, with a few corporate accounts mixed in.
Personal accounts can convey snippets of classified information, whether through carelessness or expediency. They also can lead to other more valuable targets or carry embarrassing personal details that can be used for blackmail or to recruit spies.
Drone consultant Keven Gambold, a hacking target himself, said the espionage could help Russia catch up with the Americans:
"This would allow them to leapfrog years of hard-won experience," he said.
He said his own company is so worried about hacking that "we've almost gone back in time to use stand-alone systems if we're processing client proprietary data - we're FedEx'ing hard drives around."
The AP has previously reported on Fancy Bear's attempts to break into the Gmail accounts of Hillary Clinton's presidential campaign, American national security officials, journalists and Kremlin critics and adversaries around the world.
Cover image: US Department of Defense.
More: Final RAF Airseeker Intelligence Plane Declared Fully Operational









